Managed Storage Account
To simplify the user experience, a managed storage account can be configured when setting up Retina.
Example
This example creates a Capture and stores the Capture artifacts into a storage account specified by Blob SAS URL.
- Create a secret to store blob SAS URL (and store it in blob-upload-url.txt):
kubectl create secret generic blob-sas-url --from-file=blob-upload-url=./blob-upload-url.txt
- Create a Capture YAML configuration specifying the secret created as blobUpload, this example will also store the artifact on the node host path.
apiVersion: retina.sh/v1alpha1
kind: Capture
metadata:
name: capture-test
spec:
captureConfiguration:
captureOption:
duration: 30s
captureTarget:
nodeSelector:
matchLabels:
kubernetes.io/hostname: aks-nodepool1-11396069-vmss000000
outputConfiguration:
hostPath: "/tmp/retina"
blobUpload: blob-sas-url
More Retina Capture samples can be found here.
Motivation
Retina Capture helps customers capture network packets on Kuberentes cluster to debug network issues. Before Retina Capture can debug the packets, Retina Capture can store the network packets and the customers need to download the packets from Retina Capture supported locations with tools like Wireshark.
To simplify customers' work to decide where to store the packets and then download the packets to local environment, we propose a managed account solution for customer to help customer manage the lifecycle, security when to the storage account and garbage collection of the storage account. Customers can use managed storage account by default, or specify their own storage account ID and Storage Blob Data Owner or higher privilege should be granted to AKS managed identity or service principal.
Detailed Design
Workflow
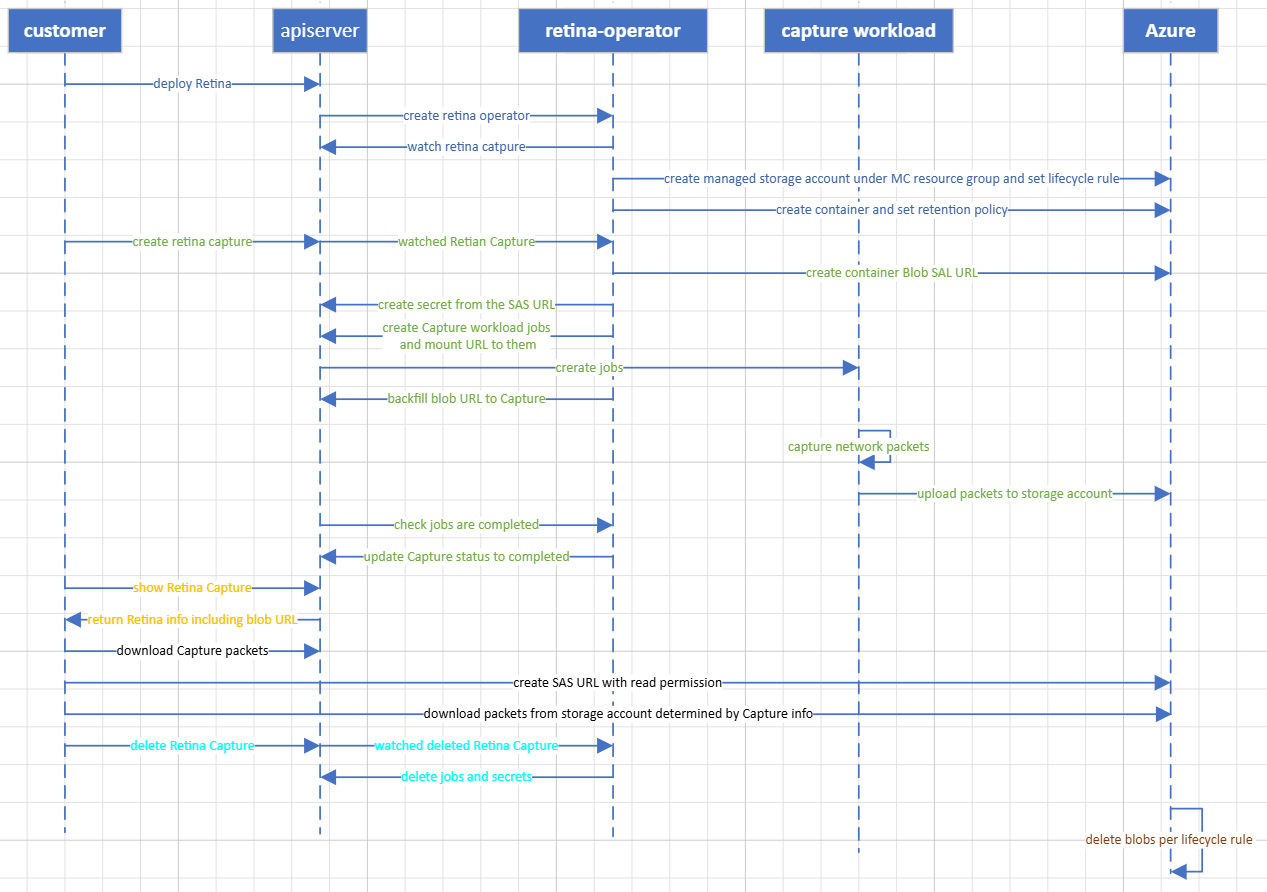
Setup
To enable the managed storage account, you need to specify the following configuration in the helm command,
TENANT_ID=""
SUBSCRIPTION_ID=""
RESOURCE_GROUP_NAME=""
REGION=""
MSI_CLIENT_ID=""
helm upgrade --install retina ./deploy/standard/manifests/controller/helm/retina/ \
--set operator.enabled=true \
--set capture.enableManagedStorageAccount=true \
--set capture.tenantId=$TENANT_ID \
--set capture.subscriptionId=$SUBSCRIPTION_ID \
--set capture.resourceGroup=$RESOURCE_GROUP_NAME \
--set capture.location=$REGION \
--set capture.managedIdentityClientId=$MSI_CLIENT_ID
Internally, enableManagedStorageAccount will change the following retina-operator configuration and azure credential config as explained in the following two sections.
Retina-Operator Configuration
enableManagedStorageAccount Configuration
enableManagedStorageAccount configuration controls whether to use managed storage account or not.
apiVersion: v1
kind: ConfigMap
metadata:
name: retina-operator-config
namespace: kube-system
data:
... ...
enableManagedStorageAccount: true/false
azureCredentialConfig: /etc/kubernetes/cloud-config/azure.json
Azure credential configuration
The configuration azureCredentialConfig in retina-operator-config indicates the Azure credential file path to talk to azure for the managed resources.
apiVersion: v1
kind: ConfigMap
metadata:
name: retina-operator-config
namespace: kube-system
data:
.. ...
enableManagedStorageAccount: true/false
azureCredentialConfig: /etc/kubernetes/cloud-config/azure.json
In the above configuration, when enableManagedStorageAccount is true, retina-operator will pick azure credential configuration from /etc/kubernetes/cloud-config/azure.json. retina-operator helm template mounts the secret containing azure credentials to /etc/kubernetes/cloud-config/azure.json.
When default storage account is enabled, a managed storage account will be created under the resource group of the sub both specified in the credential file. In the case of AKS, the resource group will be MC, or node, resource group, and subscription will be the overlay subscription.
Azure credential configuration content
Detailed explanation of the auth configuration can be found here.
Under the resource group, the service principal or managed identity should have Storage Blob Data Contributor role to create user delegation SAS, AND at least Storage Account Contributor role to manage storage account, container and polices in Azure.
- Managed Identity
{
"cloud": "AzurePublicCloud",
"tenantId": "<tenant-id>",
"subscriptionId": "<subscription-id>",
"aadClientId": "msi",
"aadClientSecret": "msi",
"resourceGroup": "<resource-group-name>", // the resource group where the cluster is deployed in
"location": "<location>", // the location where the cluster is deployed in
"useManagedIdentityExtension": true,
"userAssignedIdentityID": "<managed-identity-client-id>",
"useInstanceMetadata": true
}
- Service Principal
{
"cloud": "AzurePublicCloud",
"tenantId": "<tenant-id>",
"subscriptionId": "<subscription-id>",
"aadClientId": "<client-id>",
"aadClientSecret": "<client-secret>",
"resourceGroup": "<resource-group-name>", // the resource group where the cluster is deployed in
"location": "<location>", // the location where the cluster is deployed in
"useManagedIdentityExtension": false,
"userAssignedIdentityID": "",
"useInstanceMetadata": true
}
Storage Account
The storage account, retinacaptureUUID, is created under MC resource group and lifecycle management with 7 expiration days is created by Retina Operator if Capture is enabled. AKS customers can enable Retina Capture by upgrading their clusters after this feature is released.
Container
A container, capture, will be created to store the network artifacts after the storage account is ready. And to protect the packets from being deleted or modified, a retention policy with 7 days retention period will be applied on this container.
Create a Retina Capture
Retina-operator will create a container blob SAS URL with expiry time determined from Capture Duration to make sure blob SAS URL is invalid soon after the Capture is completed. And Retina-operator will update Capture CR with the blob SAL URL to allow the customer read the URL.